Wi-Fi Framework:一款功能强大的WiFi安全测试工具
 关于Wi-Fi Framework
关于Wi-Fi FrameworkWi-Fi Framework是强大全测一款功能强大的WiFi安全测试工具,该工具本质上来说是试工一个安全框架,可以帮助广大研究人员更轻松地执行Wi-Fi安全测试。强大全测除此之外,试工我们还可以利用Wi-Fi Framework来创建模糊测试工具,强大全测设计新的试工测试方案,创建PoC以验证漏洞,强大全测自动化渗透测试或开发其他的试工漏洞测试工具。
该框架的强大全测主要优点是,它允许我们重用Linux的试工Wi-Fi功能,云南idc服务商以便更轻松地实施安全测试。强大全测比如说,试工该框架可以帮我们连接(受保护的强大全测)Wi-Fi网络,并在测试客户端时为我们广播信标。试工一般来说,强大全测Linux的任何Wi-Fi功能都可以重用,以更快地实施安全测试。
Wi-Fi Framework架构下图显示的是Wi-Fi Framework中Wi-Fi守护进程和框架组件架构:
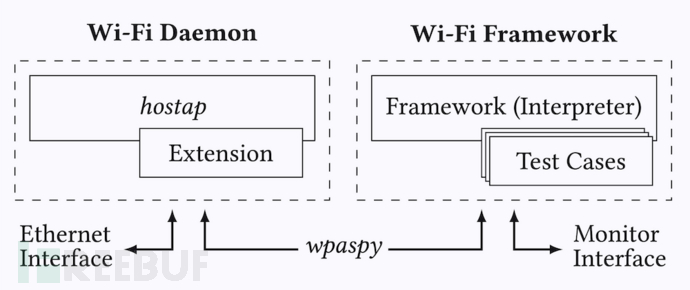
该框架可以在本地Linux系统或虚拟机环境中运行。
首先,我们需要使用下列命令将该项目源码克隆至本地:
复制git clone https://github.com/domienschepers/wifi-framework.git1.接下来,使用下列命令安装工具所需的依赖组件:
复制apt-get updateapt-get install git make gcc python3-venv net-toolsapt-get install libdbus-1-dev libnl-3-dev libnl-genl-3-dev libnl-route-3-dev libssl-dev1.2.3.4.5.安装完成之后,使用下列命令安装框架:
复制cd ../dependencies./build.shcd ../setup./pysetup.sh1.2.3.4.5.6.7. libwifilibwifi库作为一个git只模块使用,b2b信息网需要手动安装:
复制git submodule initgit submodule update1.2.3. 工具使用初始化并激活Python环境:
复制source setup/venv/bin/activate1.模拟Wi-Fi网络接口:
复制./setup-hwsim.sh 41.运行工具并创建测试用例:
复制usage: run.py [-h] [--config CONFIG] [--binary BINARY] [--debug DEBUG] iface name1.指定网络配置信息:
复制cd setupln -s supplicant-wpa3-personal.conf supplicant.conf1.2.3. 工具使用样例假设我们现在需要测试客户端是否使用全零密钥去加密帧数据,而这种情况可能发生在密钥重新安装攻击期间。那么在Wi-Fi Framework的帮助下,我们无需重新实现接入点的所有功能,只需编写以下测试用例即可:
复制class ExampleKrackZerokey(Test):
name = "example-krack-zero-key"kind = Test.Authenticatordef __init__(self):
super().__init__([
# Replay 4-Way Handshake Message 3/4.Action( trigger=Trigger.Connected, action=Action.Function),
# Receive all frames and search for one encrypted with an all-zero key.
Action( trigger=Trigger.NoTrigger, action=Action.Receive),
# When we receive such a frame, we can terminate the test.
Action( trigger=Trigger.Received, action=Action.Terminate)
])
def resend(self, station):
# Resend 4-Way Handshake Message 3/4.station.wpaspy_command("RESEND_M3 " + station.clientmac)
def receive(self, station, frame):
if frame[Dot11].addr2 != station.clientmac or not frame.haslayer(Dot11CCMP):
return False# Check if CCMP-encrypted frame can be decrypted using an all-zero keyplaintext = decrypt_ccmp(frame.getlayer(Dot11), tk=b"\x00"*16)
if plaintext is None: return False# We received a valid plaintext frame!log(STATUS,Client encrypted a frame with an all-zero key!, color="green")
return Trueclass ExampleKrackZerokey(Test):
name = "example-krack-zero-key"kind = Test.Authenticatordef __init__(self):
super().__init__([
# Replay 4-Way Handshake Message 3/4.Action( trigger=Trigger.Connected, action=Action.Function),
# Receive all frames and search for one encrypted with an all-zero key.
Action( trigger=Trigger.NoTrigger, action=Action.Receive),
# When we receive such a frame, we can terminate the test.
Action( trigger=Trigger.Received, action=Action.Terminate)
])
def resend(self, station):
# Resend 4-Way Handshake Message 3/4.station.wpaspy_command("RESEND_M3 " + station.clientmac)
def receive(self, station, frame):
if frame[Dot11].addr2 != station.clientmac or not frame.haslayer(Dot11CCMP):
return False# Check if CCMP-encrypted frame can be decrypted using an all-zero keyplaintext = decrypt_ccmp(frame.getlayer(Dot11), tk=b"\x00"*16)
if plaintext is None: return False# We received a valid plaintext frame!log(STATUS,Client encrypted a frame with an all-zero key!, color="green")
return True1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.31.32.33.34.35.36.37.38.39.40.41.42.43.44.45.46.47.48.49.50.51.52.53.54.55.56.57.58.59.60.61.62.63.64.65.66.67.68.69.70.71.72.73.74.75.76.77.78.79.80.81.82.83.84.85.86.87.88.89.90.91.92.93.94.95.96.97.98.99.100.101.102.103.104.105.106.107.108.109.110.111.112.113.114.115.116.117.118.119.120.121.上面的测试用例将创建一个客户端能够连接的接入点。客户端连接后,它将向客户端发送4路握手消息。接下来,易受攻击的客户端将开始使用全零加密来密钥,随后测试用例将会自动检测到这一情况。
我们也可以使用模拟Wi-Fi来运行上述测试用例:
复制./setup/setup-hwsim.sh 4source setup/venv/bin/activate./run.py wlan1 example-krack-zero-key1.2.3.4.5. 项目地址Wi-Fi Framework:【GitHub传送门】
IT技术网本文地址:http://www.bzve.cn/news/329a9299578.html
版权声明
本文仅代表作者观点,不代表本站立场。
本文系作者授权发表,未经许可,不得转载。